Uloq™ Core
Authentication, Authorization, Time-based One-Time Passwords, and many more features in your hand. Embrace personal security and privacy with Uloq Core.
Designed to simplify customer interactions.
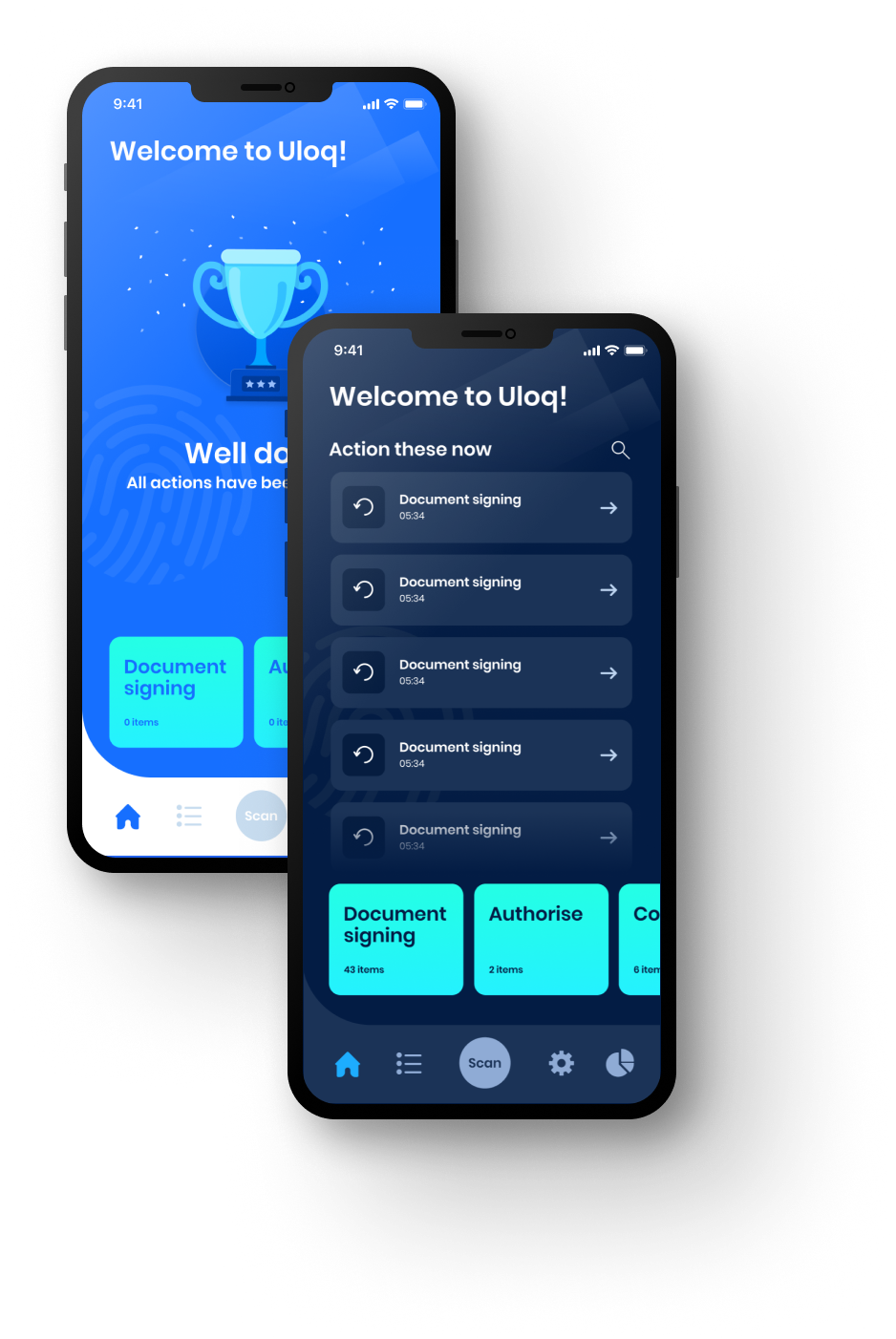
Uloq™ Core leverages your smartphone to maximize security, productivity, and peace of mind. The user-centric design of Uloq harnesses the power of your smartphone to provide you with an all-in-one cybersecurity and productivity boost. It simplifies online access using passwordless and password-free authentication. All this, while safeguarding your data with military-grade encryption and cross-device syncing.
Advanced Security
Security is an inherent part of Uloq™ Core. In a world where security is often an afterthought, Uloq™ Core is designed to securely simplify day to day transactions.
Included with...
- Leading Public Key Cryptography
- Biometric Authorization
- Environmental Authorization
- Time-based One-Time Passwords
- Distributable Encryption Keys
- Proven account recovery
- Fully auditable logs
Undeniable Identity
Uloq™ Core provides you with the tools to prove your identity to anyone, anywhere, at any time using your smartphone.
Workflow support
Uloq™ Core is designed to support your decision-making workflows by providing you with “on the go” decision approval. Saving you time and money.
Unlimited applications
Uloq™ Core is designed to be implemented into any process that requires undeniable, verifiable authorization.
Environmental Authorization
Uloq™ Core creates environmental profiles that are unique to the user. These profiles can be used to ensure that transactions are performed in a valid location.
Zero Trust
Uloq™ Core uses public key cryptography with digital signatures to ensure that all transactions are verifiable and secure.
User owned private key
Private keys are generated and owned on the user’s devices. This means that the user is in full control of their identity.
Recoverable Profile
Uloq™ Core provides a secure and proven method of recovering your profile in the event that you lose your device. Your full profile is securely backed up to the cloud and can be recovered to a new device.
How does Uloq™ work?
Uloq™ Core is designed to be implemented into any process that requires undeniable, verifiable authorization.
-
Step 1
Registration
The first time the user accesses your system, they register their Uloq™ on your system. This is a one-time process.
-
Step 2
Transaction Initiation
The transaction is started by means of the user scanning a QR Code (for an unknown user) or a push notification directly to the users device (for a known user).
-
Step 3
Transaction Approval
The user approves the transaction on their device. The user authenticated themselves using the fingerprint or facial recognition. The transaction is then digitally signed and sent back to the integrated system.
-
Step 4
Transaction Verification
The transaction is verified using the public key of the user. This ensures that the transaction was signed by the user and that the transaction has not been tampered with.
Price Suit to Your Business
Integrate Uloq™ today and secure your business.
Get our any Services
With Suitable Pricing
Contact us today! Our knowledgeable sales team is ready to craft an affordable package that is tailored to your organization's specific needs and budget.
Uloq Core
$1/user
- 10 Users
- Authorization & Authentication
- QR Code Generation
- Push Notifications
Get Started Now
Enterprise
Custom Pricing
- On-Premise or Cloud
- Service Level Agreement
- Customized Pricing
- Built for Scale
- Self managed or managed by Eccenscia
Frequently Asked Questions
Want to know more about Uloq™ Core?